How to Sandbox Apps in Linux Systems
Sometimes nosotros take to run an application that we exercise not trust, but we are afraid that it might look at or delete our personal information, since fifty-fifty though Linux systems are less prone to malware, they are not completely immune. Maybe you desire to admission a shady-sounding website. Or perchance you lot need to access your depository financial institution account, or any other site dealing with sensitive private information. Yous might trust the website, but do not trust the add-ons or extensions installed in your browser.
In each of the above cases, sandboxing is useful. The idea is to restrict the non-trusted application in an isolated container -a sandbox – then that it does not have access to our personal information, or the other applications on our system. While in that location is a software chosen Sandboxie that does what we demand, it is only available for Microsoft Windows. But Linux users need non worry, since we have Firejail for the job.
So without further ado, allow u.s. see how to prepare Firejail on a Linux organization and use information technology to sandbox apps in Linux:
Install Firejail
If you are using Debian, Ubuntu, or Linux Mint, open the Terminal, and enter the following command:
[sourcecode]sudo apt install firejail[/sourcecode]
Enter your account password, and press Enter. If you are asked for a confirmation, blazon y, and press Enter once again.
If yous are using Fedora, or any other RedHat-based distribution, just replace apt with yum. The rest of the instructions remain the aforementioned:
[sourcecode]sudo yum install firejail[/sourcecode]
You are at present ready to run Firejail.
Optional: Install the Graphical Interface
Y'all can cull to install the official graphical front-end for Firejail chosen Firetools. Information technology is non available in the official repositories, and so nosotros will have to manually install information technology.
ane. Download the installation file for your system. Debian, Ubuntu and Mint users should download the file ending with .deb . I am on a 64-bit Mint installation, then I selected firetools_0.ix.40.1_1_amd64.deb.
2. Later the download is complete, open the Concluding, and navigate to your Downloads folder past running cd ~/Downloads.
iii. Now install the Firetools package by running the command sudo dpkg -i firetools*.deb.
4. Enter your countersign, hitting Enter, and y'all're washed.
Bones Usage
In a Terminal, write firejail, followed past the command that you need to run. For example, to run Firefox:
[sourcecode]firejail firefox[/sourcecode]
Make sure to close all Firefox windows first. If you lot don't, it will just open a new tab or window in the current session – negating any security benefit y'all would get from Firejail.
Similarly, for Google Chrome:
[sourcecode]firejail google-chrome[/sourcecode]
Running commands like this gives the awarding access to only a few needed configuration directories, and your Downloads folder. Access to the rest of the file organization, and the other directories in your Home folder is restricted. This tin be demonstrated by trying to admission my home folder from Chrome:
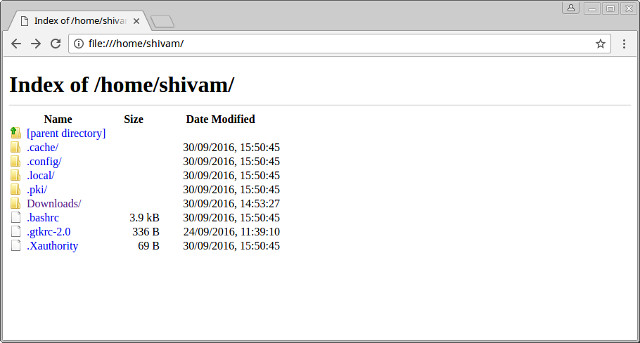
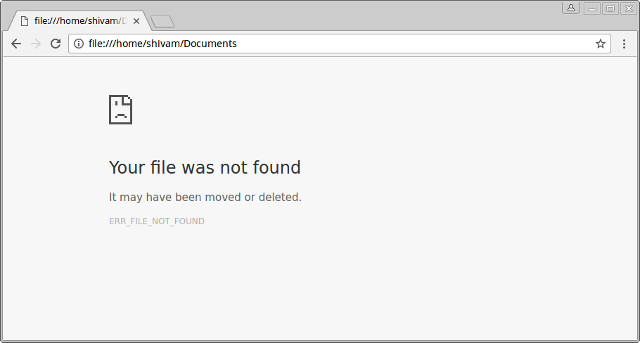
As y'all can encounter, most of my folders, including Pictures, Documents, and others are not accessible from the sandboxed chrome. If I nevertheless try to access them by modifying the URL, I will get a File not found mistake:
Restricting Applications Further
Sometimes, you might need more restrictions, for example, you may want to apply a completely fresh browser profile with no history, and no add-ons. Let'due south say you don't want your web browser to access your Downloads folder either. For that, we can use the private pick. Run the awarding as follows:
[sourcecode]firejail google-chrome –individual[/sourcecode]
This method completely restricts the application – it ever starts in a fresh state, and can non even create or download whatsoever new files.
Using the Graphical Interface – Firetools
If y'all prefer to use a GUI instead of running a command every time, you can use the graphical forepart-stop for Firejail chosen Firetools. Open up the Concluding, and run the control firetools. Yous will run into a window similar this:
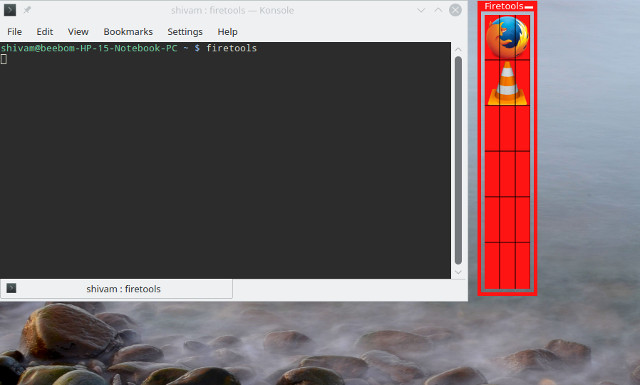
You can double click on any pre-configured application (Firefox and VLC here) to run it sandboxed. If you want to add an application, correct click on an empty space on the Firetools app, and click on Edit:
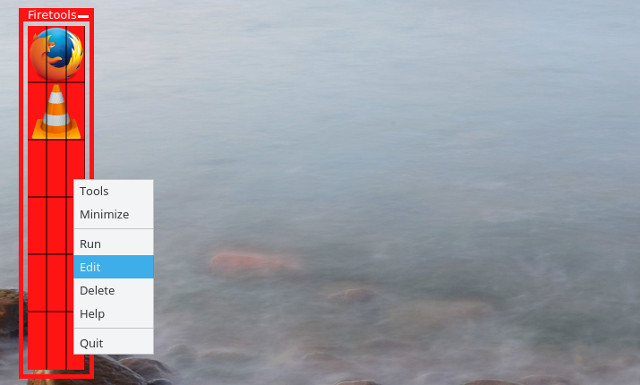
You can now enter the name, clarification, and the command that you want to run. The command would exist the aforementioned as you lot would run in a console. For example, to create an icon for Google Chrome that yous want to run in private mode, y'all would input the post-obit:
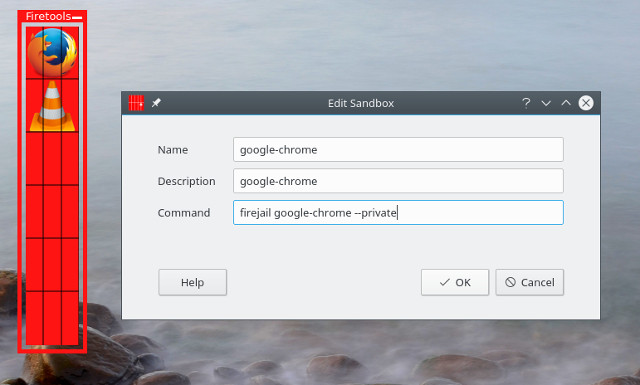
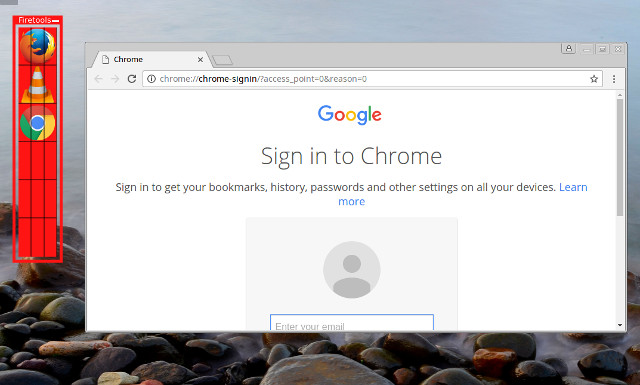
Now simply double-click the icon yous just created to launch the app:
SEE ALSO: 10 Of import Tips to Keep Your Android Device Secure
Run Doubtful Applications Securely On Linux With Firejail
That is it from our side when information technology comes to sandboxing not-trusted apps in Linux with Firejail. If you lot wish to learn more than near the advanced sandboxing options that Firejail offers, accept a await at the official documentation. What practise yous use Firejail for? Has it saved you from malicious applications or websites? Make sure to let us know past dropping us a line in the comments section below.
Source: https://beebom.com/how-sandbox-non-trusted-apps-linux-systems/
Posted by: hugheypastachis.blogspot.com


0 Response to "How to Sandbox Apps in Linux Systems"
Post a Comment